Threat actors continually use new and sophisticated methods to identify vulnerabilities in company networks. These weaknesses can pose significant financial and reputational risks if left unaddressed.
So, how can you manage and mitigate security risks in your organization?
Implement an IT risk management framework — a structured approach to identifying, assessing, and mitigating security risks.
Read on to learn more about IT risk management frameworks and the benefits of implementing them. We’ll cover five different frameworks that can help protect your IT infrastructure and ensure compliance with regulations.
What is an IT risk management framework?
An IT risk management framework is a set of processes and procedures that organizations follow to identify, assess, and mitigate cybersecurity threats. It helps companies manage risk, comply with industry regulations, and improve their security posture.
Why is an IT risk management framework important?
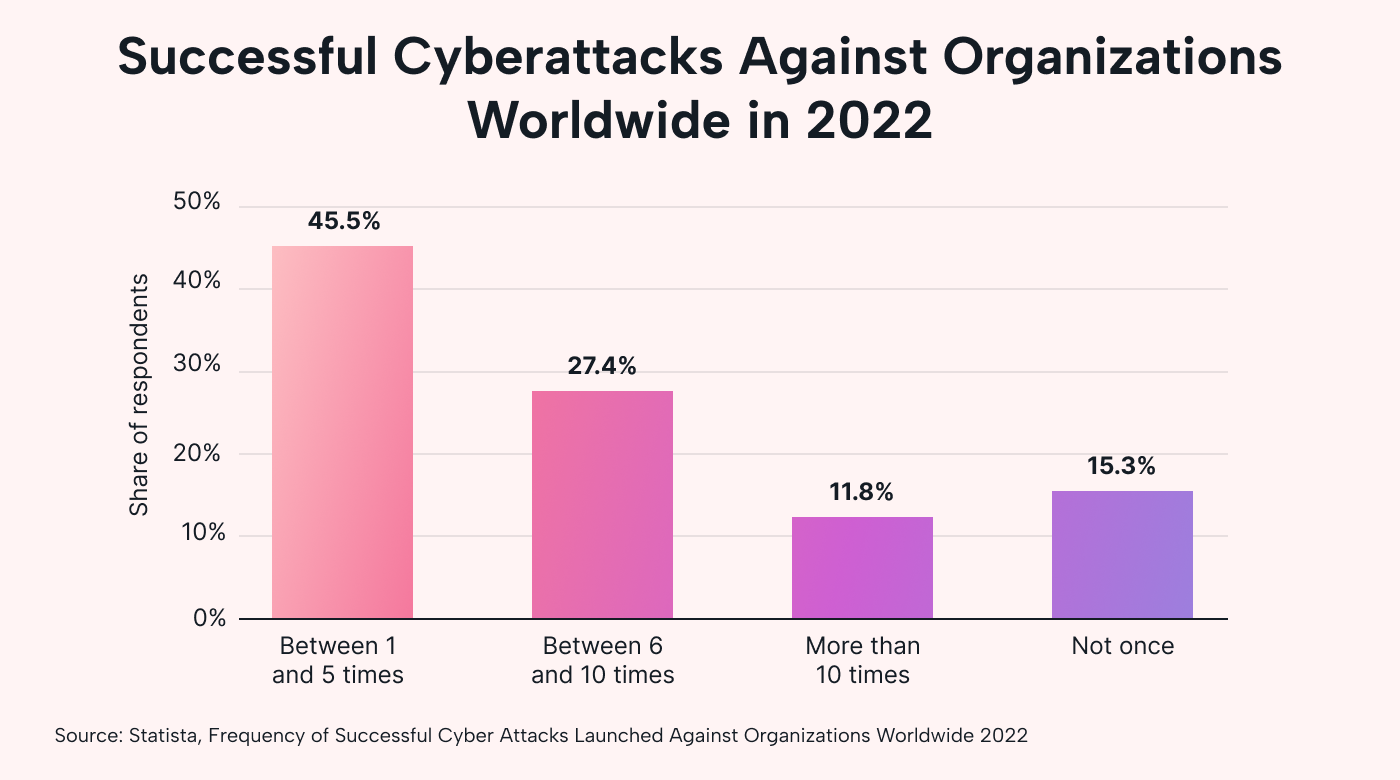
Cyberattacks are on the rise. In 2022, 45% of IT security professionals reported one to five successful attacks against their company’s network in the past 12 months.
And the situation is likely worsening. Another report revealed an 8% increase in global weekly cyberattacks in the second quarter of 2023 — the highest in two years.
 |
Threat actors are always advancing their tactics, too. Recent research from McAfee shows a rise in “voice phishing,” a type of scam that uses AI software to impersonate a friend or family member.
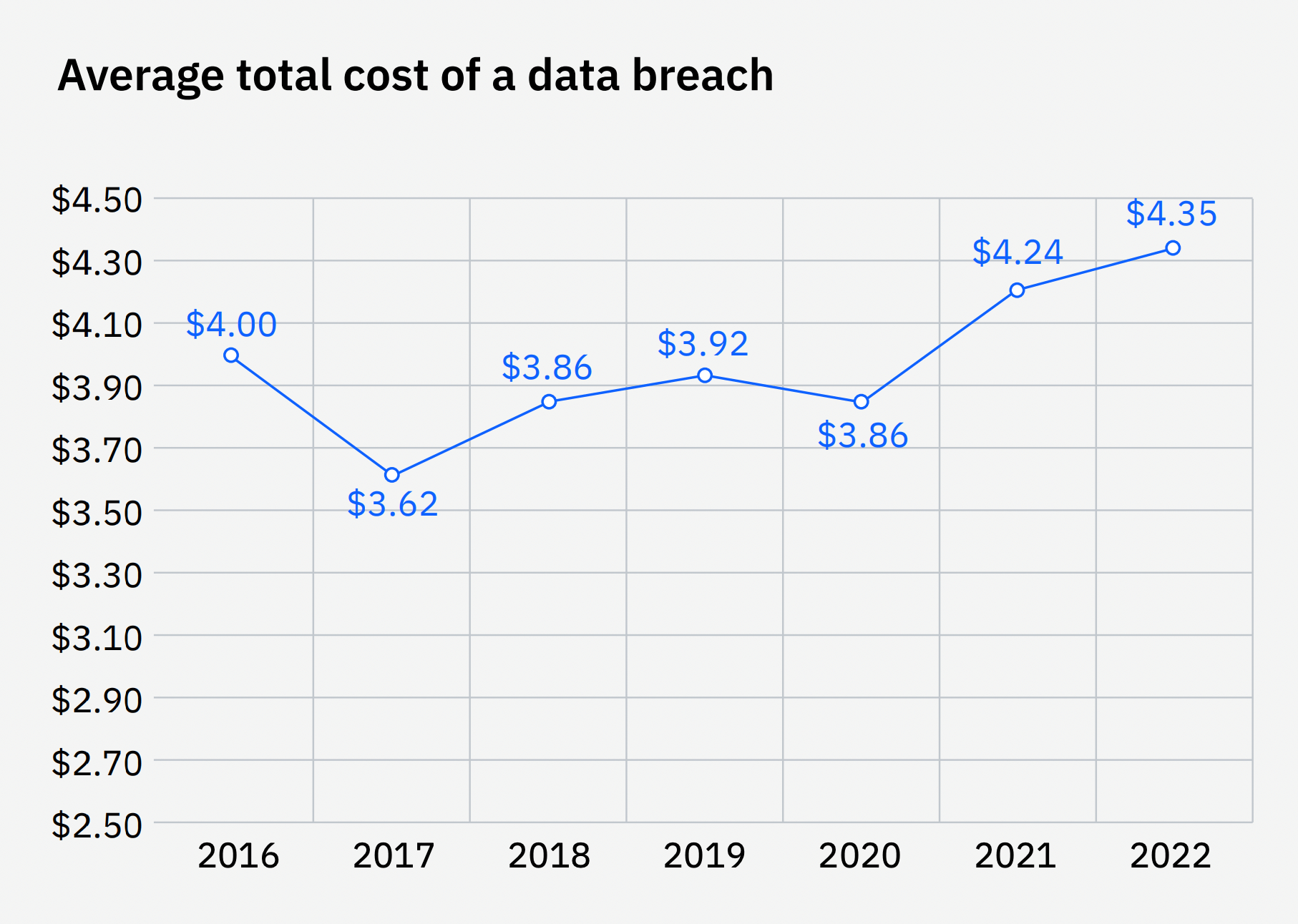
A successful breach can have devastating financial consequences. The average total cost of a data breach is $4.35 million. These breaches can also disrupt your business operations while you deal with them, potentially causing more ongoing revenue loss.
Given this evolving threat landscape, companies must adopt a multi-layered approach to cybersecurity to successfully mitigate risks.
Benefits of an IT risk management framework
Every company faces some degree of risk, but implementing an IT risk management framework can help mitigate cybersecurity risks. Here’s how:
Enhances security posture
An IT risk management framework provides guidance for how companies can improve their security posture by analyzing potential risks and taking steps to mitigate them.
For example, an IT risk management framework may recommend a zero-trust architecture to reduce the number of exploitable attack vectors. Zero-trust policies ensure that only authorized users can use network assets because access will be aggressively denied at multiple points throughout the network unless users validate their credentials.
This is just one example of how an IT risk management framework can help companies secure their network.
Improves decision-making
IT risk management frameworks provide a structured approach for prioritizing risks. For example, a risk assessment reveals two potential threats: a network breach and a supply chain disruption.
While you want to address both, you may only have enough resources to tackle one first. But which one should you prioritize?
You can assess each risk’s potential impact and likelihood with an IT risk management framework. If the supply chain disruption is considered a higher risk, you can immediately minimize its impact.
Ensures compliance with industry regulations
Many industries mandate security requirements that companies must comply with.
The Health Insurance Portability and Accountability Act (HIPAA) is a good example. Healthcare providers must implement appropriate physical and technical measures to protect health information.
Violating these regulations can lead to huge penalties. Lifetime Healthcare Companies agreed to pay $5.1 million for a data breach that affected over 9.3 million people.
Adopting an IT risk management framework can help with any industry compliance requirements.
5 IT risk management frameworks
Here are the top IT risk management frameworks you can consider. Each has strengths and weaknesses, so choosing one that aligns with your company’s needs is essential.
1. NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) developed the NIST Cybersecurity Framework to help US federal agencies reduce cybersecurity risks. However, organizations can adopt the framework to improve their security posture.
The NIST Cybersecurity Framework consists of seven key steps:
- Prepare: Companies take steps to prepare their organization to manage risks. They identify risk management roles, determine an acceptable level of risk, and establish governance structures to guide decision-making.
- Categorize: Organizations categorize information systems based on the data they store and process. This helps assess the potential impact of a breach.
- Select: Organizations determine and select appropriate security controls to protect information systems. One example is NIST SP 800-53, which provides a list of controls to maintain the confidentiality and integration of data.
- Implement: Companies implement and integrate the selected security controls into their information systems. This step includes properly testing all privacy controls.
- Assess: Companies assess and test control systems to determine if they operate as intended. They may conduct penetration tests to identify areas for improvement.
- Authorize: A senior official authorizes the continued operation of information systems. It involves making informed decisions based on residual risks.
- Monitor: Companies continue to monitor their information systems to identify and detect threats. This step involves implementing monitoring tools and analyzing security logs.
2. ISO 31000
The International Organization for Standardization (ISO) developed the ISO 31000, which provides guidelines to help organizations in different verticals manage risks.
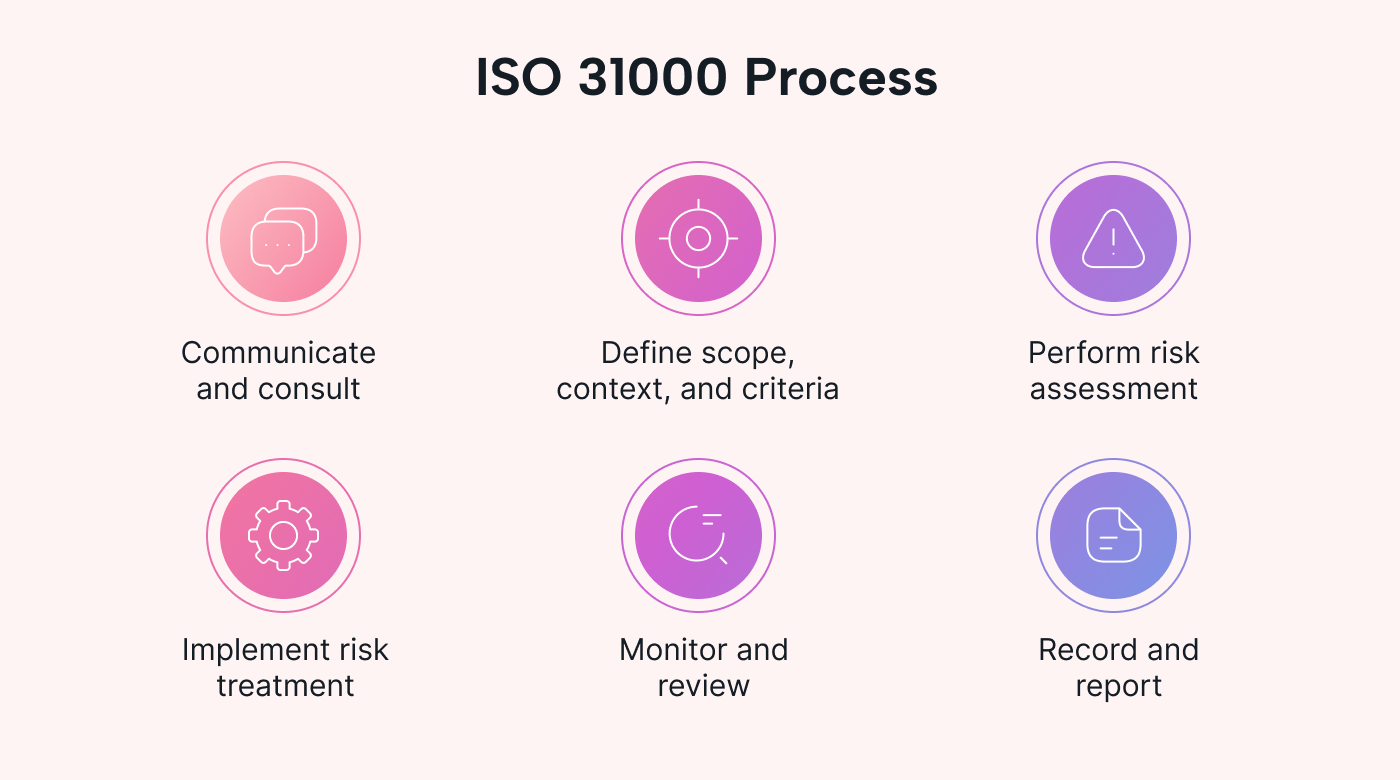 |
The ISO 31000 consists of six steps:
- Communicate and consult: Getting buy-in from relevant stakeholders is a must to support risk management efforts. This helps ensure a smooth implementation.
- Define scope, context, and criteria: Scope defines the boundaries of all risk management activities, while context considers any factors that may affect the risk management process. Criteria refers to the conditions in which risks are evaluated and accepted.
- Perform risk assessment: This step involves identifying, analyzing, and evaluating potential risks, as well as estimating the likelihood and impact of those risks. Companies can use these assessments to prioritize risks based on their significance.
- Implement risk treatment: This involves developing and implementing risk treatment strategies to manage and mitigate identified risks.
- Monitor and review: Risk management isn’t a one-time ordeal. This step involves regularly monitoring and reviewing the effectiveness of risk treatment strategies.
- Record and report: Maintaining accurate records is essential for accountability. This step aims to document all risk management activities and outcomes to keep relevant stakeholders informed.
3. Control Objectives for Information and related Technology (COBIT)
ISACA, a global nonprofit focusing on IT governance, developed the COBIT framework to help organizations align their IT activities with their objectives. It provides companies with a robust IT governance framework and bridges the gap between:
- Technical issues
- Business risks
- Control requirements
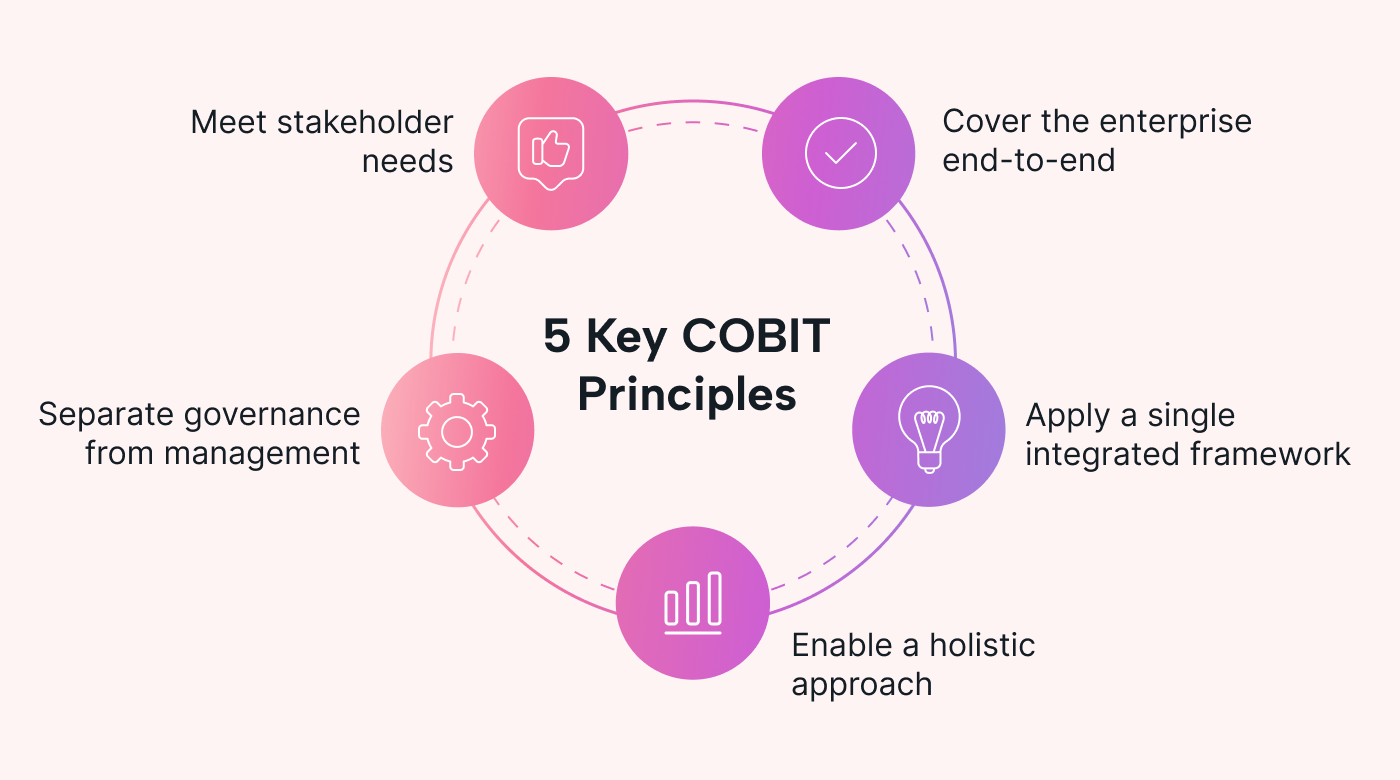 |
The COBIT framework consists of five key principles:
- Meet stakeholder needs: COBIT emphasizes the importance of aligning IT activities with the needs of stakeholders. This helps organizations ensure that IT initiatives, including risk management efforts, align with business goals.
- Cover the enterprise end-to-end: COBIT recognizes that IT processes and systems are deeply connected. This principle promotes a holistic approach to IT risks and implementing proper controls across the enterprise.
- Apply a single integrated framework: Too many frameworks can lead to inconsistencies in IT governance. Adopting a single framework can help organizations streamline and unify their IT processes.
- Enable a holistic approach: COBIT encourages organizations to consider all aspects of IT when managing risks, including people, business processes, and technology.
- Separate governance from management: Governance focuses on aligning IT initiatives with objectives, while management focuses on day-to-day operations. The distinction can help companies establish more effective governance structures.
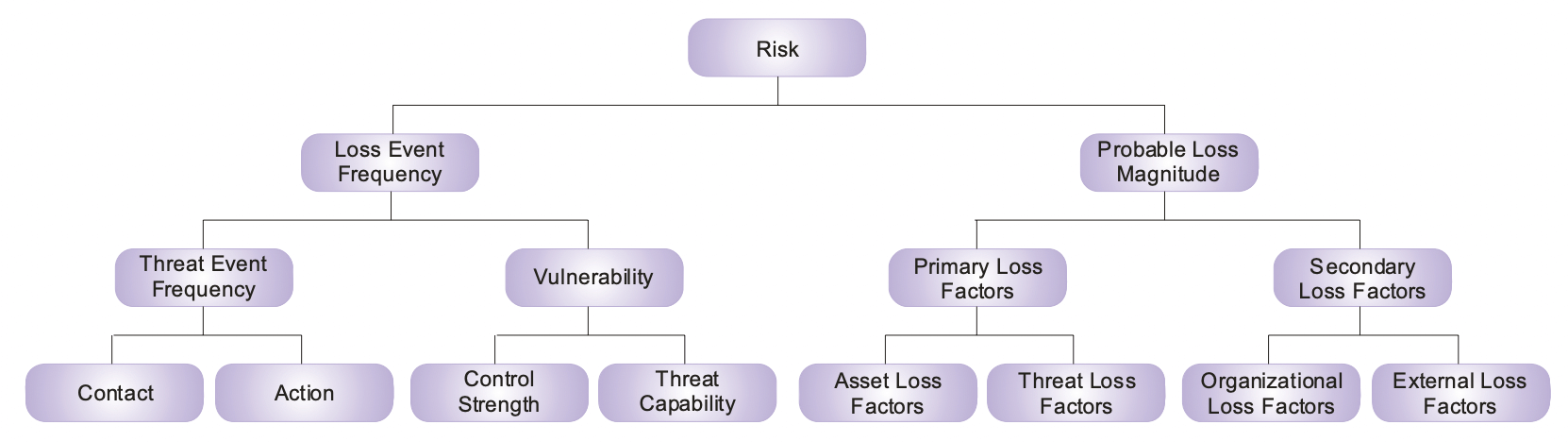
4. Factor Analysis of Information Risk (FAIR)
FAIR takes a more quantitative approach to risk management. It involves analyzing and quantifying risks in monetary terms. The benefit here is you can communicate hard numbers behind certain risks to stakeholders and enable better decision-making.
The FAIR framework consists of four stages:
- Identify assets: The first step involves identifying all assets and determining their associated risks. Examples can include hardware, software, and other assets.
- Evaluate loss event frequency (LEF): The second step involves estimating the likelihood and frequency of a loss event. Companies can analyze historical data and conduct risk assessments to calculate these figures.
- Evaluate probable loss magnitude (PLM): The third step involves calculating estimated losses for worst-case and likely scenarios. This is done by considering lost revenue and remediation costs.
- Articulate the risks: The last step involves articulating the risks and turning them into actual figures. Companies may use simulation models to consider all risk factors.
5. Information Technology Infrastructure Library (ITIL)
ITIL is a framework that describes best practices for planning, delivering, and maintaining IT services. It describes several processes for risk management.
These processes include:
- Risk management support: This includes defining roles and responsibilities, establishing risk management policies, and allocating adequate resources to risk management efforts.
- Business impact and risk analysis: This involves conducting a business impact analysis and prioritizing threats based on severity.
- Assessment of required risk mitigation: This involves developing and allocating resources to risk mitigation strategies. The goal is to mitigate the impact of potential risks and ensure business continuity.
- Risk monitoring: This involves continuously monitoring the effectiveness of risk mitigation strategies and making appropriate corrections accordingly.
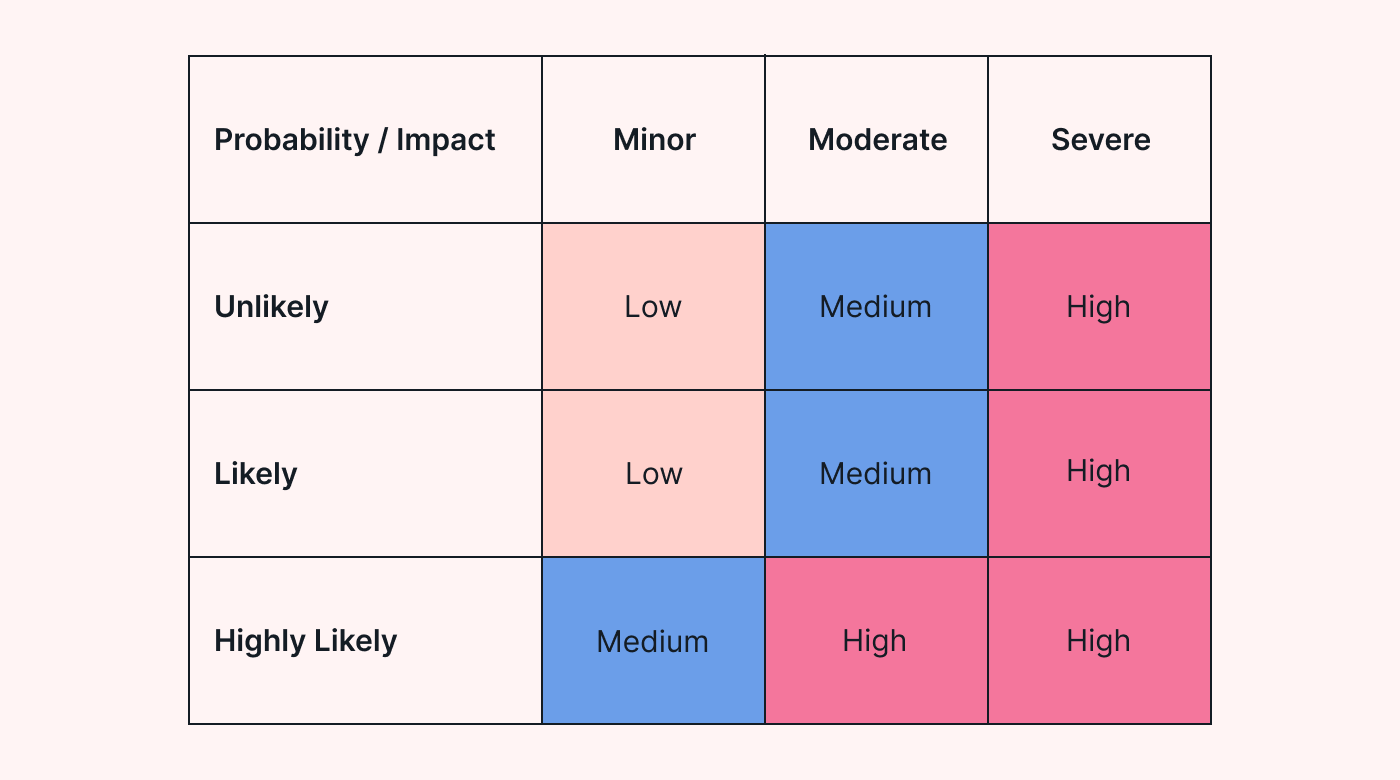
Companies can then combine these processes with a risk matrix to prioritize risks based on their likelihood and severity.
 |
ITIL focuses primarily on IT service management (ITSM), but companies can adapt the risk management processes it describes to anticipate and mitigate risks.
Automate risk prioritization with automation software
Cyber threats are an ongoing challenge for all businesses. With an IT risk management framework, companies can greatly mitigate risks and enhance their security posture.
However, coordinating your risk management efforts is a huge undertaking. It involves identifying risks, assessing their impact, developing mitigation strategies, and measuring their effectiveness.
So, how can you organize all your tasks in one place? How can you optimize your team’s schedules and prioritize critical work?
Try Motion free for the next seven days. It’s a powerful productivity tool that uses automation and AI to customize your schedule and find ways to save you more time.